
Referrer-Policy header security is a request header that indicates the site which the traffic originated from. If there is no adequate prevention in place, the URL itself, and even sensitive information contained in the URL will be leaked to the cross-site.
The Referrer-Policy header is a fairly new header that has been a W3C Candidate Recommendation since January 26, 2017. It makes it possible to control which referrer information is included in requests. When viewing a page, the referrer information indicates the origin of the request. Because this can lead to privacy and security issues when passing on the URL, the Referrer-Policy header was created to control how this information is sent from a referring page to the target page in the course of browsing.
Referrer-Policy is important because it addresses the following issues:
• Unexpected cross-origin information leakage hinders web users’ privacy. A protective referrer policy can help.
• Consider setting a referrer policy of strict-origin-when-cross-origin. It retains much of the referrer’s usefulness, while mitigating the risk of leaking data cross-origins.
• Don’t use referrers for Cross-Site Request Forgery (CSRF) protection. Use CSRF tokens instead, and other headers as an extra layer of security
Referrer-Policy Header Security Working Model
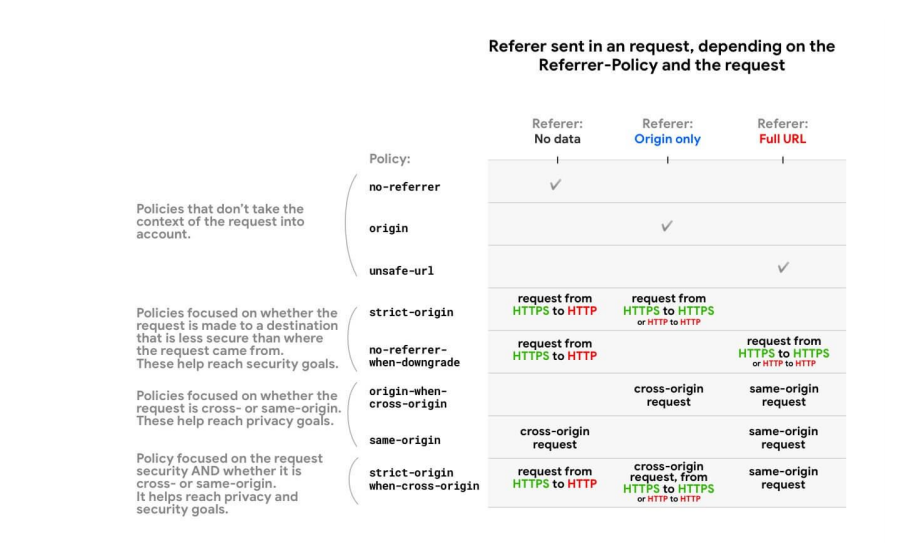
All Referrer policies that take the scheme (HTTPS vs. HTTP) as (strict-origin, no-referrer when-downgrade and strict-origin-when-cross-origin) treat requests from an HTTP origin to another HTTP origin The same way as requests from an HTTPS origin to another HTTPS origin—even if HTTP is less secure. That's because for these policies, what matters is whether a security downgrade takes place, as if the request can expose data from an encrypted origin to an unencrypted one. An HTTP → HTTP request is unencrypted all along, so there is no downgrade. HTTPS → HTTP requests, on the contrary, present a downgrade. If a request is same-origin, this means that the scheme (HTTPS or HTTP) is the same; hence there is no security downgrade
How to integrate Referrer-Policy Header Security
The Referrer-Policy HTTP header governs which referrer information, sent in the Referer header should be included with requests made.
How to integrate Referrer-Policy Header Security give as below
Syntax: • Referrer-Policy: no-referrer • Referrer-Policy: no-referrer-when-downgrade • Referrer-Policy: origin • Referrer-Policy: strict-origin • Referrer-Policy: origin-when-cross-origin • Referrer-Policy: strict-origin-when-cross-origin • Referrer-Policy: same-origin • Referrer-Policy: unsafe-url
[1] How to add in Nginx configuration file There are following code need to add in Nginx configuration file add_header Referrer-Policy "strict-origin-when-cross-origin"; [2] How to add in Apache configuration file There are following code need to add in Apache configuration file header Referrer-Policy "strict-origin-when-cross-origin" [3] How to add in .htaccess file There are following code need to add in .htaccess configuration file <IfModule mod_headers.c> Header set Referrer-Policy "strict-origin-when-cross-origin" <IfModule mod_headers.c>
There are following steps, where each Referrer-Policy has been described detailed view • no-referrer: This sends no referrer information along with the request made. • no-referrer-when-downgrade: This sends complete URL information to a potentially trustworthy URL from modern HTTPS State or from not modern HTTPS state to any origin . Information is sent for HTTPS -> HTTPS and HTTP -> HTTPS transition . This is the default Referrer-Policy. • origin: It only sends the origin value of the request client when making either same origin (same website) or cross-origin (different website) requests. • strict origin: This only sends origin information to potentially trustworthy URL from modern HTTPS State or from not modern HTTPS state to any origin. • origin-when-cross-origin: It sends complete URL information when making requests on same origin but only origin information when making cross-origin requests. • strict-origin-when-cross-origin: It sends complete URL information when working on request from same origin. It sends only origin information to potentially trustworthy URL from modern HTTPS State or from not modern HTTPS state to any origin. No referrer information is sent to a potentially non-trustworthy URL. • same-origin: It sends referrer information when origin is on same website but no information is sent for cross origin. • unsafe-url: It sends complete URL information irrespective of any criteria.
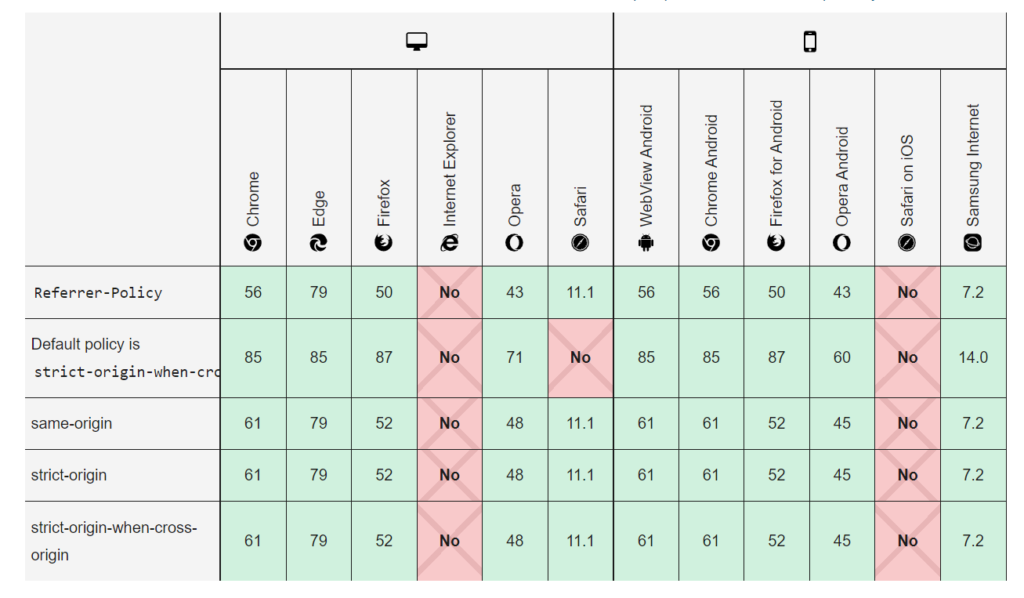
There are following list of Referrer-Policy’s Browser compatibility, that is why Referrer-Policy must be integrate
There are following below advantages after integrating Referrer-Policy Header Security
- HTTPS sites will never transmit referrer information to non-HTTPS sites.
- Referrer Policy is used to determine what information is sent along with the requests.
- The Referrer-Policy header on your server to control what information is sent through the Referrer header security. For example, a directive of no-referrer would omit the Referrer header security entirely.
- The Referrer HTTP request header contains an absolute or partial address of the page making the request.
- The Referrer Policy HTTP header sets the parameter for amount of information sent along with Referer Header while making a request.
- Referrer policy is used to maintain the security and privacy of source account while fetching resources or performing navigation
- This could also be a way to increase the integrity for the users of the website. For example, if a user reads a news article about cats and the article has a link to a cat shelter website.
HTTP Security Headers Checker Tool
https://www.site2info.com/sitesecurity.php
Other Important HTTP Security Headers
Magento 2 All Database Tables [500 & more Tables]
HTTP Security Headers Checker Tool – Security Headers Response
How to add Feature-Policy Security Header
How to add X-Content-Type-Options Security Header
How to add Expect-CT Security Header
How to add X-Frame-Options Security Header
How to add X-XSS-Protection Security Header
How to add Referrer Policy Security Header
Referrer Policy Header Security
How to add HTTP Strict Transport Security (HSTS)
How To Set CSRF Token in Magento 2
