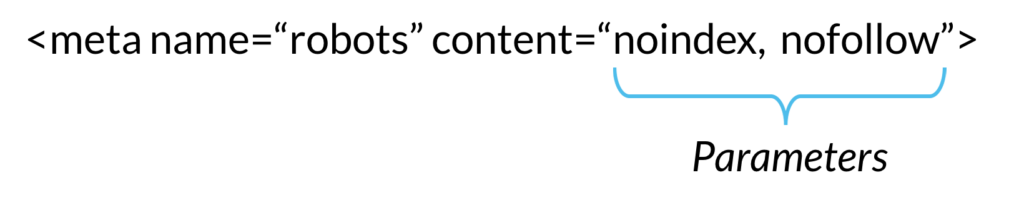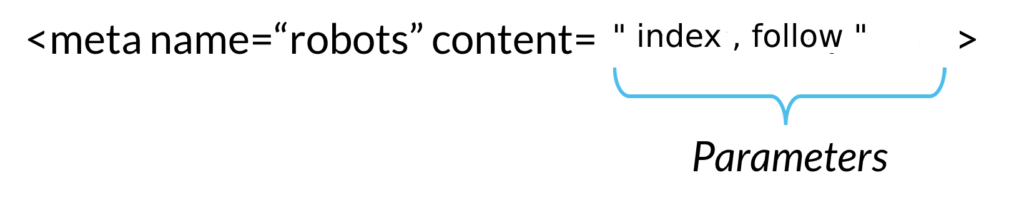There are following below methods to add Feature-Policy Security Header in Apache or NGINX or .HTACCESS
[1] How to add in Nginx configuration file There are following code need to add in Nginx configuration file add_header set Feature-Policy "geolocation 'self'; vibrate 'none'"; [2] How to add in Apache configuration file There are following code need to add in Apache configuration file header always set Feature-Policy "geolocation 'self'; vibrate 'none'" [3] How to add in .htaccess file There are following code need to add in .htaccess configuration file <IfModule mod_headers.c> Header set Feature-Policy "geolocation 'self'; vibrate 'none'" <IfModule mod_headers.c>
Syntax: Feature-Policy: <directive> <allow-list> There are following below things, according, website need, can enable/disable Feature-Policy • Directive: This header accepts 2 directive but on directive can redirect with other directives, as mentioned and described below: • <directive>: It corresponds to the instructions on how we can use different features and API’s. • <allow-list>: It is a list indicating that how the browser feature can be used. • <directive>: This directive can redirect to any of the following directive: • • accelerometer: Used to get information about acceleration of device • ambient-light-sensor: Used to get information whether there is enough light in surroundings • autoplay: Used to control media autoplay settings. Mostly used with audio and video elements • battery: Used to get the status of battery using Battery Status API • camera: Used to control video input via a camera of device • display-capture: Captures screen contents through a screenshot • document-domain: Used to control the current document’s document domain by setting it or unsetting it • encrypted-media: Used to control Encrypted Media Extension API (EME) • fullscreen : Used to control full screen access • geolocation: Used to show location of user on a map by using geolocation API • gyroscope: Used to get information about orientation of device accessing gyroscope of device • layout-animations: Used to show layout animations and transitions • legacy-image-formats: Displays image in legacy format • magnetometer: Used to get information about magnetic orientation of device • microphone: Used for audio input through device’s microphone • midi: Used to access Web MIDI API • oversized-images: Used in displaying and downloading large over-sized images • payment: Controls all payment related activity by using Payment Request API • picture-in-picture: Allows a video to play in Picture-in-Picture mode • public key-credentials-get: Uses Web Authentication API and retrieves public-key credentials • sync-xhr: Used in making synchronous XMLHTTPRequest • usb: Controls WebUSB API for USB Media access • wake-lock: Informs the device to not enter power-saving mode by using Wake Lock API • xr-spatial-tracking: Used to interact with WebXR session by making use of WebXR Device API
HTTP Security Headers Checker Tool
https://www.site2info.com/sitesecurity.php
Magento 2 All Database Tables [500 & more Tables]
HTTP Security Headers Checker Tool – Security Headers Response
How to add Feature-Policy Security Header
How to add X-Content-Type-Options Security Header
How to add Expect-CT Security Header
How to add X-Frame-Options Security Header
How to add X-XSS-Protection Security Header
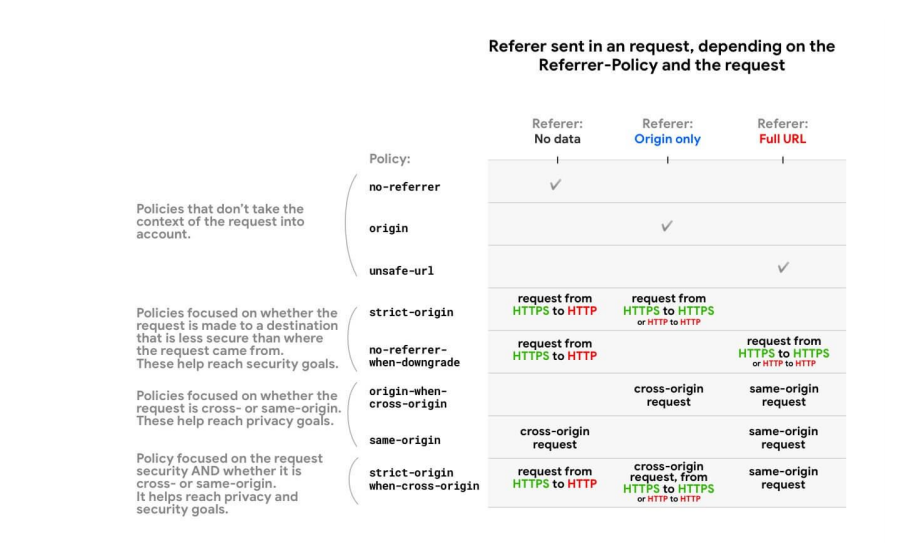
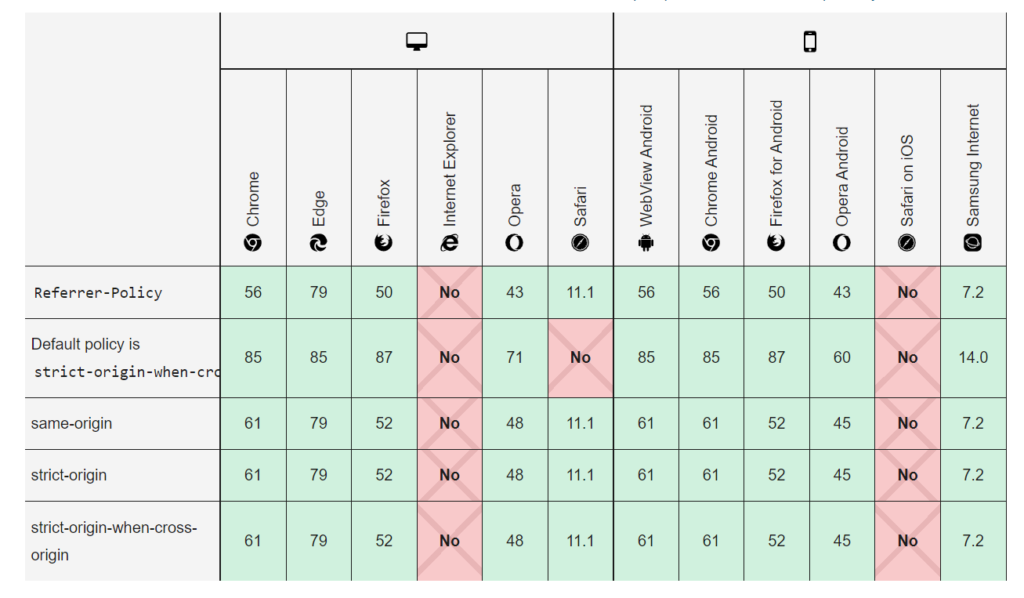
How to add Referrer Policy Security Header
Referrer Policy Header Security
How to add HTTP Strict Transport Security (HSTS)
How To Set CSRF Token in Magento 2